Conversion Boosting Extensions How’s your business looking? Is your revenue where you want it to be? Are you converting enough website visitors into customers? Many entrepreneurs are looking for something new to try, something to elevate their business, raise their game, and achieve big revenue growth.So we’ve compiled this list of...
Top 5 WordPress URL Shortener Plugin in 2022 If you’re a regular blogger or an affiliate marketer, you know the importance of short URLs.Long URLs often appear ugly, not the look you want on a professional website. However, you can make your links less bulky and easier to share with...
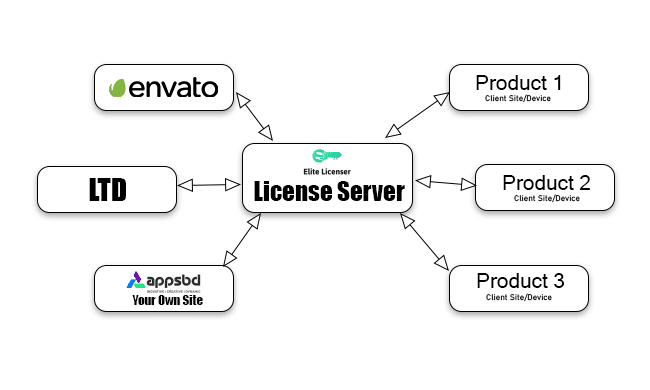
Elite Licenser Addon - For WooCommerce Elite Licenser addon is an add-on of woocommerce which is also an add-on of Elite Licenser. It is used to generate license code for woocommerce digital products. Users can see the license code in order details. Elite Licenser Addon has ability to disabled License...
Elite Licenser Addon - For WooCommerce Elite Licenser addon is an add-on of woocommerce which is also an add-on of Elite Licenser. It is used to generate license code for woocommerce digital products. Users can see the license code in order details. License auto disabled when an order is refunded,...
Mystery of TypeScript TypeScript is a wonderful tool for writing JavaScript that scales. It’s more or less the de facto standard for the web when it comes to large JavaScript projects. As outstanding as it is, there are some tricky pieces for the unaccustomed. One such area is TypeScript discriminated unions....
Elite Licenser API Many people make the mistake of inputting the API of Elite License in Postman. Many people give api_key input of get parameter instead of body parameter of post request. And then the elite licenser, gives an error, The API key doesn’t have this operation’s permission.Today we will...
Ultimate List of WooCommerce PluginOnline stores are the best thriving business option in today's market. A fully functional WooCommerce store can take your business to great heights. Here is the list of all the must-have plugins for your WooCommerce store to flourish in the market and save your time from...
WooCommerce is one of the world’s most popular online store builders. This free, open source plugin comes with all the essentials for setting up an eCommerce venture, and it can be installed on any self-hosted WordPress website. WooCommerce adds basic retail functions to any compatible WordPress theme, but online entrepreneurs can...
10 Jobs Coding has long been thought of as a world of computer nerds -- from video game designers to IT specialists. For years the media has focused on coding as a path chosen separately from traditional careers. However, many of those representations date back to before the widespread usage...
In this modern world, the technologies have shifted drastically! Some languages and technologies have seen downfall over the period of time, whereas some of them have broken the bars! Python is one of those languages that is at its peek and does not seem to stop in this race in...